Recent surveys show that data security is one of the top concerns among executives and top-level government officials. Data security is a rather generic term and means different things to different people, but everyone agrees that in its most basic form it means protecting data from unwanted actions from unauthorized users. The data that needs to be protected ranges from data stored on a social network site to top-secret information about people and projects stored in a governmental datacenter. The consequences of this data being released ranges from people being mildly embarrassed to, in the case of top-secret governmental data, people being put in harm’s way.
In the past couple of years, we have seen an increase in the number of data security breaches, and we have witnessed the very real consequences of these breaches. Top level employees have been fired, huge fines have been imposed on companies, stock prices have dropped, and people have begun to doubt our ability to protect information entrusted to us.
The problem of data being released is so great that the European Union (EU) has taken a tough stand on the protection of a person’s data and has enacted the General Data Protection Regulation (GDPR), which has very serious consequences for the release of personal data—regardless if it was released through a malicious security breach or inadvertently.
We have many techniques and policies in place to try and stop nefarious attempts to access data, but the reality is a large percent of data security issues have been accidental. These range from a storage system that have not had the correct security policies and tools implemented on them to devices that have not been properly purged of data. The industry has come up with a term to describe data that should be secure but has been placed on an insecure device; data spillage.
Different situations can lead to data spillage: There are the obvious ones, such as a file being moved to an unauthorized location or an email sent to the wrong person. One would think that you could delete the file and the problem would be solved. However, the reality is that it is far more problematic and far more difficult to contain once it has occurred.
The problem with deleting a file is that it does not actually remove the data from the disk; it only removes the name associated with the location of the data. A gross simplification of this would be going into a bookstore and removing the cover from a book, leaving the rest of the book on the shelf. The information in the book will still be available; it will just be a little tougher to find. Various programs and techniques have evolved over the years that allow you to recreate files from the data left on the device on which it was stored. This allows unauthorized users to recover data and perform unwanted actions with that data after it has been “deleted.”
Programs have been designed to overwrite the actual data on the device, but complicating matters is that flash-based (SAS and NVMe SSDs) devices are far different than traditional HDD when it comes to deleting data. Whereas a HDD can overwrite data, flash devices cannot overwrite data – they must erase the old data before new data can be written to it. The process of erasing data on a flash device takes a relatively large amount of time and so, instead of waiting for the erase operation to take place, a flash device will simply move “erased” data out of the way and then opportunistically erase it during slack times. Doing this allows flash devices to maintain their write speeds during normal operations. This can be problematic when trying to truly delete a file from a flash device as the erase may not have taken place and the data may still reside on the flash device.
The reconstruction of data from “deleted” files is not a theoretical concept; in 2016 a study was conducted by purchasing used disks bought off eBay and Craigslist. This study showed that 2/3 of the secondhand disks they had acquired had recoverable information on them, including names and social security numbers. There are various governmental and industrial standards to ensure that the data on a storage device is completely unreadable. The most common of these is to do multiple overwrites of the physical location on the device where data has been written. The overwriting of devices of large capacity is time consuming and if any area of a device cannot be overwritten, the entire device must be destroyed.
In some cases after data spillage has been detected, IT departments have had to take away the storage system, in order to evaluate the threat of the data being released. It could take days or even weeks to resolve the issue. During that time the users would not have access to other data that was stored on the system.
Fortunately, NetApp realized this was a problem and when they released ONTAP 9.4 in May of 2018, they put in a new security feature to deal with issues such as this. In the remainder of this article we will take a look at one of these features, Secure Purge. Secure Purge cryptographically shreds files on a NetApp Volume Encryption (NVE), allowing you to non-disruptively “scrub” data on these volumes, ensuring that data cannot be recovered from the physical media and thereby ensuring that data spillage will not inadvertently take place.
How Secure Purge Works
Secure Purge uses a multi-step process to completely remove data from the physical media of the encrypted volume on which a file that was deleted resided on; this includes data from any garbage-collection processes. First, Secure Purge deletes all Snapshot copies in the volume. If the volume is the source of a SnapMirror relationship, the SnapMirror relationships must be broken before the volume can be purged and any busy Snapshot copies on the volume must be released. Once snapshot issues have been addressed, Secure Purge triggers a volume move that re-encrypts the files that reside on the volume data with a new key. The old key is destroyed, ensuring that purged data cannot be recovered from the storage media.
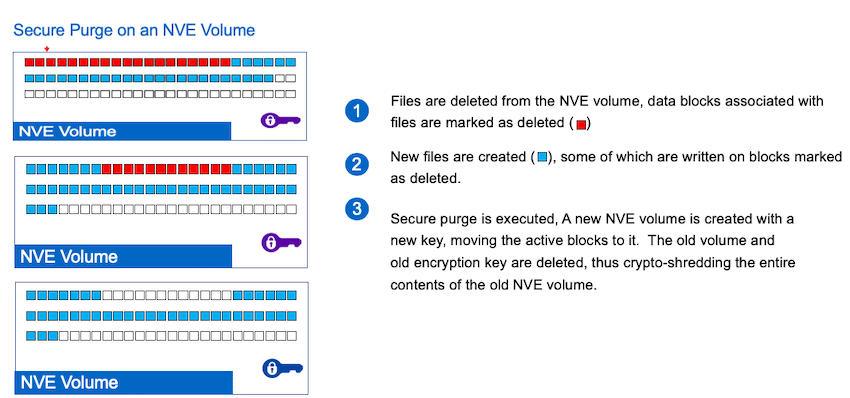
Depending on the amount of data the volume has on it Secure Purge may take just a few minutes to several hours to complete.
Running Secure Purge
Only cluster administrators are allowed to run Secure Purge. Once you have entered an advanced-privilege level you can then enter volume encryption secure-purge start -vserver SVM_name -volume volume_name to start the secure purge process.
For example, to securely purge the deleted files on vol1 on SVM vs1, you would enter:
cluster1::> volume encryption secure-purge start -vserver vs1 -volume vol1
This will trigger a volume move that re-encrypts the remaining unpurged data with a new key on the current storage aggregate. Once the data move is completed, the old key is automatically destroyed, ensuring that purged data cannot be recovered from the storage media.
To examine the status of a Secure Purge operation, enter: volume encryption secure-purge show
For example, to see the status of the Secure Purge operation on cluster1 you would enter:
cluster1::> volume encryption secure-purge show
If you need to abort a Secure Purge, you enter: volume encryption secure-purge abort
For example, to see the abort the secure-purge operation on cluster1, you would enter:
cluster1::> encryption secure-purge abort
Final Thoughts on Secure Purge
In order to certify that Secure-purge worked as advertised, NetApp had Ontrack (a data recovery specialist and founding member of the International Data Sanitization Consortium) use their Erasure Verification Service to try to recover data from a NetApp flash array that had Secure Purge run on it. Ontrack was unable to recover any system or user data from any of the flash devices, including the flash devices’ over-provisioned area on the array. Ontrack verified and ensured that the Secure Purge data sanitization process was effective. At the 2019 Flash Memory Summit, Ontrack and NetApp were presented with the Most Innovative Flash Memory Enterprise Business Application award. NetApp was recognized for creating the Secure Purge feature, while Ontrack received the award for the validation they performed on the feature with their Erasure Verification Service. The full Ontrack report is available here.
To put it bluntly, if you have any data on your system that is classified or confidential, you should be using a tool such as Secure Purge to ensure that it is totally inaccessible after it has been “deleted.” NetApp hinted that governments and the military are the largest users of Secure Purge, but obviously commercial enterprises can see the value in it.
Secure Purge is included with every version of ONTAP from 9.4 and newer. As strange as it seems, we have not seen any other primary storage vendors offer a feature with the capabilities as Secure Purge. However, we believe that with the current emphasis on security, customers will soon be demanding such a feature. At this point, NetApp has a strong lead within the industry when it comes to fighting data spillage with Secure Purge.
New Data Security and Privacy Features in ONTAP 9.4
This report was sponsored by NetApp. All views and opinions expressed in this report are based on our unbiased view of the product(s) under consideration.




 Amazon
Amazon