EMC recently commissioned a data protection index that highlighted various cyber threats. The study was conducted by the independent Vanson Bourne and looked at enterprise backup in 18 countries around the world. EMC states that the index shows business have been doing well at protecting against the best known threats but are unprepared for upcoming attacks. In order to help companies with these future attacks, EMC is releasing its new Isolated Recovery Solutions.
Cyber attacks are on the rise, from the infamous hack of Linkedin social medai site to smaller attacks that are less likely to get much coverage. Organizations in all industries are being targeted and most attacks are coming through end-user devices. Once security is breached, data can be compromised or damaged before security has time to react. EMC believes that recovery is key to getting a business up and running once more after suffering an attack. And they go on to state that isolating the recovery data adds another layer of protection.
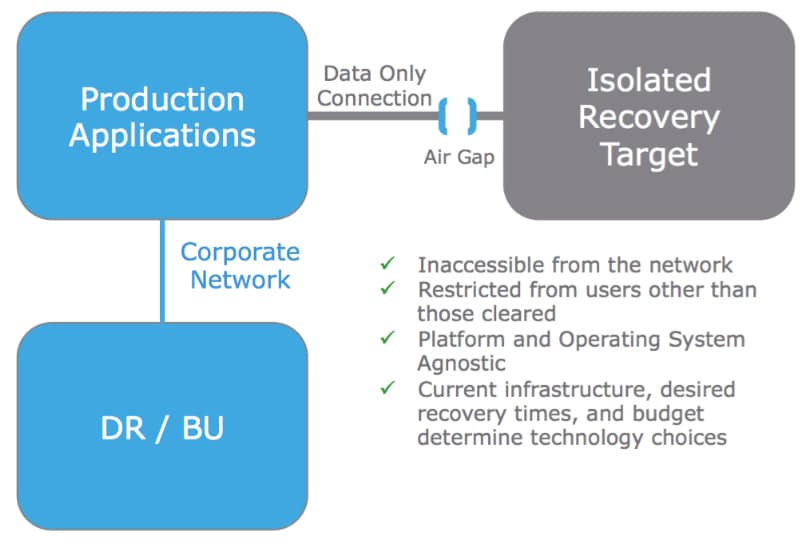
EMC has broken the process down to a few key points to best help organizations recover from a cyber attack. First companies need to plan out the solutions needed, selecting the application candidates, recovery time, and recovery point objectives. The next step, and arguably the most critical, is to have an isolated data center environment for the mission-critical data. This environment needs to be disconnected form the network and only accessible by users with proper clearance. With the isolated environment, schedules need to be in place for data copies and “air gaps” between the isolation zone and production, this process can and probably should be automated. The copy data in the isolation zone needs to be checked for possible issues such as malware. And then procedures need to be set in place for recovery after an incident.
While it is most likely impossible for companies to be 100% protected against cyber attacks, EMC’s Isolated Recovery Solution listed above should help companies to recovery quickly from a possible breach.
Availability
EMC Isolated Recovery Solutions are available now for most products with support for XtremIO, Unity, and Isilon technologies expected in the near future.




 Amazon
Amazon