With the escalation in malware and ransomware hacks, everyone in the industry is sensitive to implementing iron-clad security features. VMware is answering that call with NSX-T 3.2 that includes not only security enhancements but also networking and cloud deployment. We wrote about all the new features and enhancements in a previous post.
NSX-T 3.2 introduces new features to identify and respond to malware and ransomware attacks in the network, enhance user identification and L7 application identification capabilities, and, at the same time, simplify deployment.
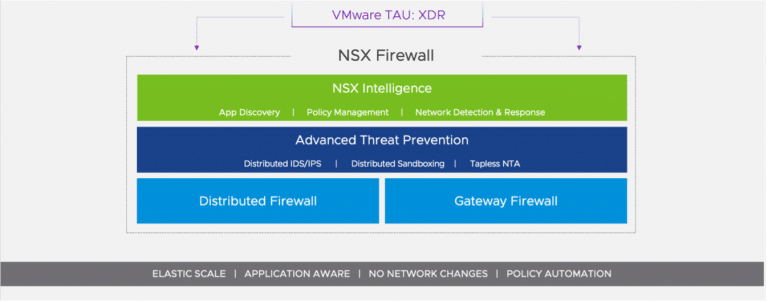
VMware NSX 3.2 Security – Distributed Advanced Threat Prevention (ATP)
Techniques to hack into network devices have continued to become more sophisticated. Not satisfied with a single attack process, these attackers often use multiple techniques to penetrate the network, moving laterally within the network and stealing critical data. Prior methods to thwart these hackers were at best micro-segmentation solutions focused solely on access control reducing the attack surface but certainly not enough to provide protection against the technologies used today.
VMware NSX-T 3.2 introduces several new capabilities focused on the detection and prevention of attacks inside the network. At one time, this type of security would require a physical network tap, for each network segment. These hardware taps would be network disruptive and, if a failure occurred, it would mean a heavy lift to replace the tap. Not efficient at all.
NSX-T Distributed Malware Prevention
Lastline dynamic malware technology, acquired by VMware in 2020, is integrated with NSX Distributed Firewall delivering a Distributed Malware Prevention solution. With Lastline integrated within the hypervisor kernel, the embedded firewall identifies both “known malicious” as well as “zero-day” malware. This is a big improvement over previous methods of defending against new versions of malware.
Distributed Behavioral IDPS
While Intrusion Detection and Prevention System (IDPS) delivered primarily signature-based detection of intrusions, NSX 3.2 introduces “behavioral” intrusion detection capabilities as well. This capability alerts administrators when a workload is seeing behavioral anomalies, like DNS tunneling or beaconing, for example, that could be a cause for concern.
Network Traffic Analysis (NTA)
Distributed Network Traffic Analysis (NTA) gets introduced in NSX-T 3.2. NTA is used for baselining network-wide behavior and identifying anomalous behavior at the aggregated network level. Network-wide anomalies like lateral movement, suspicious RDP traffic, and malicious interactions with the Active Directory server, for example, can alert security teams about attacks underway and help them take quick remediation actions.
Network Detection and Response (NDR)
As useful as ML/AI is in creating new techniques in security detection and prevention, hackers are using the technology to circumvent existing security tools. This leads to alert overload, and resulting fatigue. Let’s look at this a little deeper since AI/ML seems to be everywhere.
AI vs ML
Artificial intelligence tries to replicate intelligent, human-like behavior. This can be achieved using machine learning. An AI system that does not include machine learning is considered an expert system since the skills are based upon a captured series of rules.
Machine Learning is a specific type of AI. ML systems analyze large data sets, categorize the data, and create rules about what belongs in what category. ML can be used to analyze network behavior data and categorize it as normal or anomalous based on a defined set of rules.
Machine Learning comes in two flavors: supervised and unsupervised. Supervised ML involves mapping input variables to output variables in order to make accurate predictions about the data being analyzed. When used as threat detection, ML algorithms could use suspicious behaviors and a “malicious” category assignment for developing a threat classifier, then use that classifier to analyze new samples.
In unsupervised ML, the system clusters groups of data together, based on that data’s features. The result is the identification of groups with similar elements, allowing an analyst to handle a large number of similar samples based on a single decision.
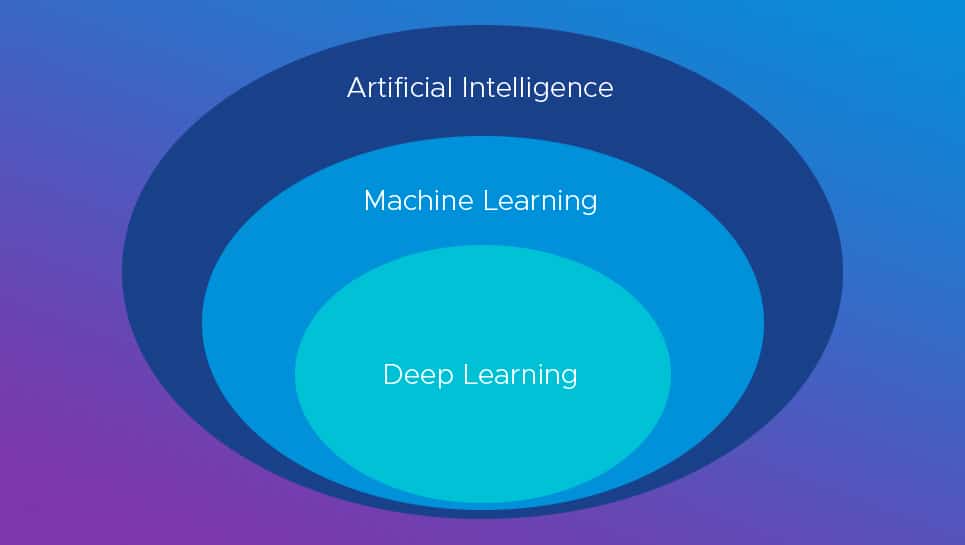
And then there’s deep learning: a specific type of machine learning that uses neural networks instead of statistical analysis for analyzing data. Deep learning is particularly good at finding classifications in large amounts of data. But deep learning is disadvantaged by its reduced explanatory power as to why something belongs in a particular grouping, such as why an executable is dangerous.
Just as vendors attempt to create secure systems using AI/ML tools, so do the hackers in the world. They use the data they collect to date and create malicious behavior. This is referred to as adversarial learning, and developers must define those types of attacks and create blocks to prevent them from intruding on the system.
Leveraging advanced AI/ML techniques, the NSX-T 3.2 Network Detection and Response solution consolidates security IOCs from different detection systems like IDS, NTA, malware detection. etc., to provide a ”campaign view” that illustrates specific attacks in play at that point in time. MITRE ATT&CK visualization helps customers see the specific stage in the kill chain of individual attacks, and the ”time sequence” view helps understand the sequence of events that contributed to the attack on the network.
Key Firewall Enhancements
While delivering Advanced Threat Prevention capabilities in NSX-T 3.2, providing meaningful enhancements for core firewalling capabilities is an equally critical area of innovation.
Prior to NSX-T 3.2, workloads connected to both overlay-based N-VDS switch ports as well as VLAN-based switch ports, customers had to move the VLAN switch ports from VDS to N-VDS before a Distributed Firewall could be enforced. With NSX-T 3.2, native VLAN DVPGs are supported as-is, without having to move to N-VDS. Effectively, Distributed Security can be achieved in a completely seamless manner without having to modify any networking constructs.
With NSX-T 3.2, Distributed Firewall rules can be created and modified natively within vCenter. For small- to medium-sized VMware customers, this feature eliminates the need to leverage a separate NSX Manager interface.
NSX supported user identity-based access control in earlier releases. The ability to connect directly to Microsoft Active Directory supporting user identity mapping is been introduced in this new release. For customers who do not use Active Directory user authentication, NSX supports VMware vRealize Log Insight as another method to carry out user identity mapping. This feature enhancement is applicable for both NSX Distributed Firewall as well as NSX Gateway Firewall.
Enhanced L7 Application Identification for Distributed and Gateway Firewalls
The signature set is now enhanced to about 750 applications. Unlike perimeter firewall vendors, the focus with NSX is on internal applications hosted by enterprises rather than internet application identification. This feature enhancement is applicable for both NSX Distributed Firewall as well as Gateway Firewalls.
NSX Intelligence
NSX Intelligence delivers visibility for all application traffic inside the network. Administrators create micro-segmentation policies to reduce the attack surface. The processing pipeline de-dups, aggregates, and correlates East-West traffic to deliver in-depth visibility.
With the growth of application infrastructure, the security analytics platform must grow with it. This new release moved the service from a stand-alone appliance to a containerized micro-service architecture powered by Kubernetes. This architectural change future-proofs the NSX Intelligence data lake and will eventually scale out the solution to n-node Kubernetes clusters. This update makes NSX Intelligence a fit for large enterprises, especially with the scale-out feature.
NSX Gateway Firewall
While NSX Distributed Firewall focuses on east-west controls within the network, NSX Gateway Firewall is used for securing ingress and egress traffic into and out of a zone.
NSX Gateway Firewall in the 3.2 release is updated with significant Advanced Threat Detection capabilities. Gateway Firewall can now identify both known as well as zero-day malware ingressing or egressing the network. This new capability is based on the Gateway Firewall integration with Lastline’s highly reputed dynamic network sandbox technology.
Internal users and applications reaching out to malicious websites is a huge security risk that must be addressed. In addition, enterprises need to limit internet access to comply with corporate internet usage policies.
NSX Gateway Firewall in 3.2 can also restrict access to internet sites, preventing internal users from accessing malicious sites based on either the category the URL belongs to or the “reputation” of the URL. The URL to category and reputation mapping is constantly updated by VMware so even after many changes in the internet sites, customer intent is enforced automatically.
Summary
NSX-T release 3.2 makes significant enhancements to existing NSX-T security. Updates to NSX Gateway Firewall address the ongoing threat from outside hackers but also addresses the need to police internal access to outside websites. One of the more interesting updates to this release is around AI/ML and how it is being utilized to analyze traffic and perform intelligent IDPS, NTA, NDR functions. This provides administrators with the tools to prevent the ever-present hacking threat.





 Amazon
Amazon