With the release of Proxmox VE 7.1 comes a lot of impressive new or improved features, some of the most impressive being security-related. Some of those features are new and exciting, and others simply being quality of life updates that make employing better security practices easier than ever before. In this piece, we take a deep dive into some of the latest Proxmox VE 7.1 security enhancements and updates.
Proxmox VE 7.1 Security – TPM and UEFI Secure Boot
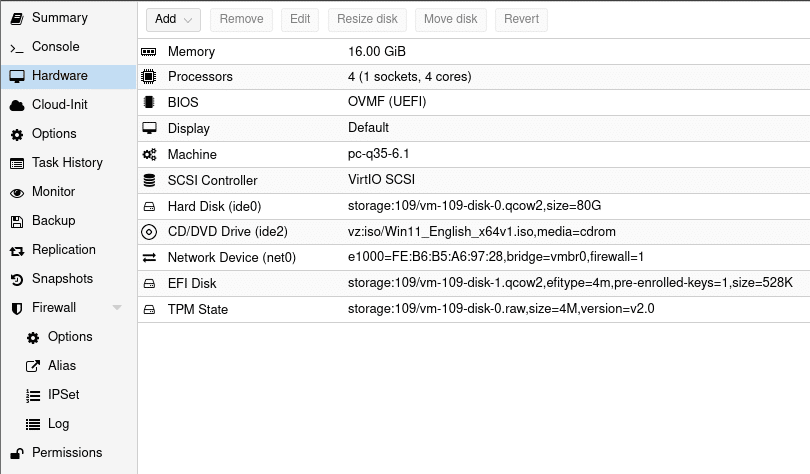
The most notable security feature in this update is official Trusted Platform Module (TPM) 2.0 support. Before the update, it was possible, but it required installing 3rd party packages. TPM 2.0 allows the user to install Operating Systems that require it, or simply benefit from it, most notably being Windows 11. To add TPM when creating a VM, simply enable it, select your storage, and choose what version you want.
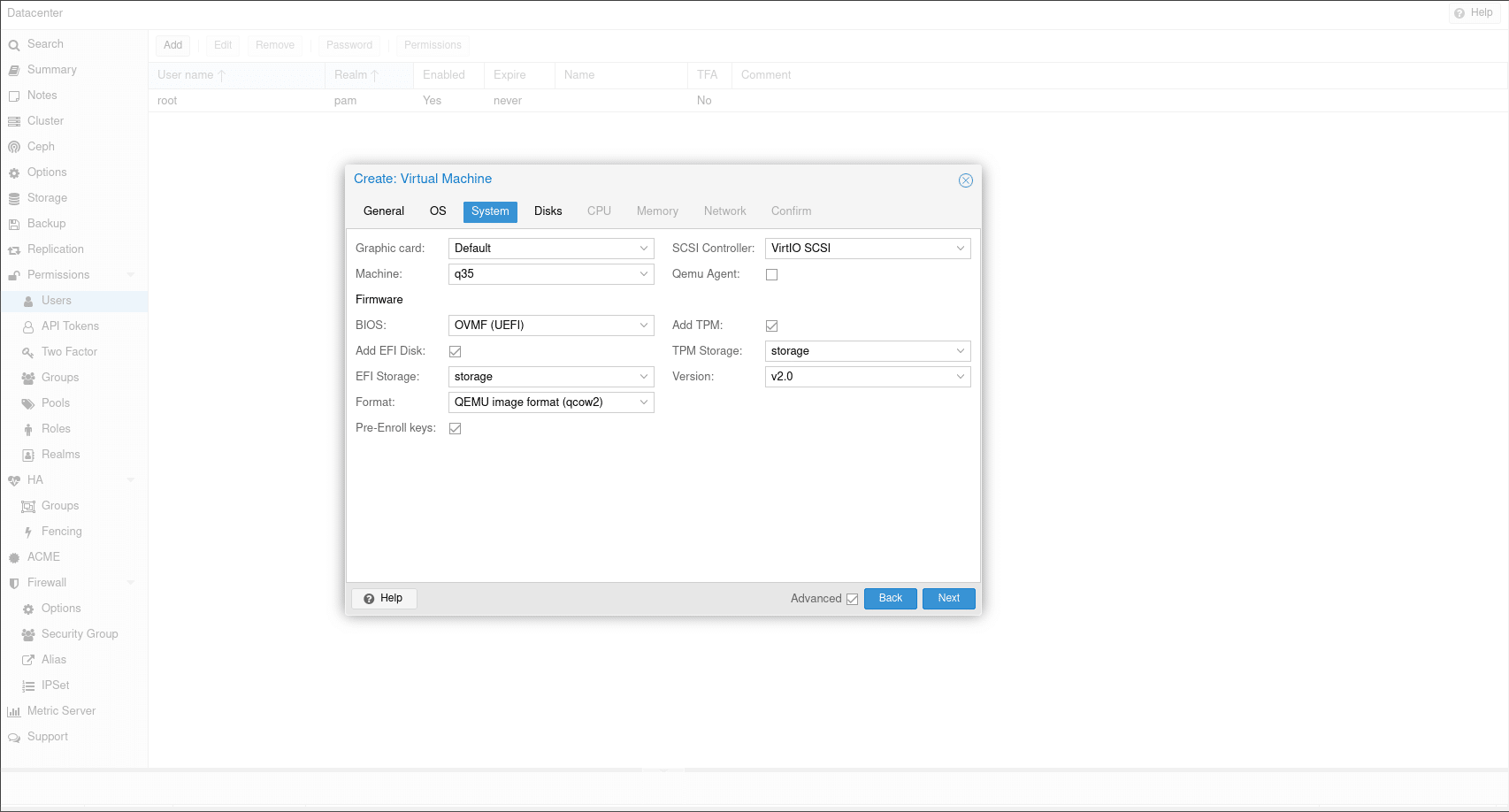
Linux and Windows both can take advantage of TPM 2.0, it can be used to store keys for disk encryption, as a random number generator, and more. Proxmox having support for it opens up a lot of doors when it comes to development and testing.
Additionally, Proxmox now has secure boot functionality built into the UI. Newly created VMs have the option to enable said feature, with an option for pre-enrolling Microsoft and popular Linux distribution keys available.
Two-factor Authentication
The new update also features significant 2FA quality of life improvements. First and foremost, the addition of one-time recovery keys is huge, they serve as a way into an account if you lose or are otherwise unable to access your 2FA method, whether that be a YubiKey (which Proxmox supports) or a TOTP app on your phone. Basically, it is a list of 10 codes that can only be retrieved upon generation that you can input in place of a 2FA method; once used, they cannot be used again. The option of only using one-time recovery keys as your only 2FA method also exists, but in reality, probably is a very poor choice.
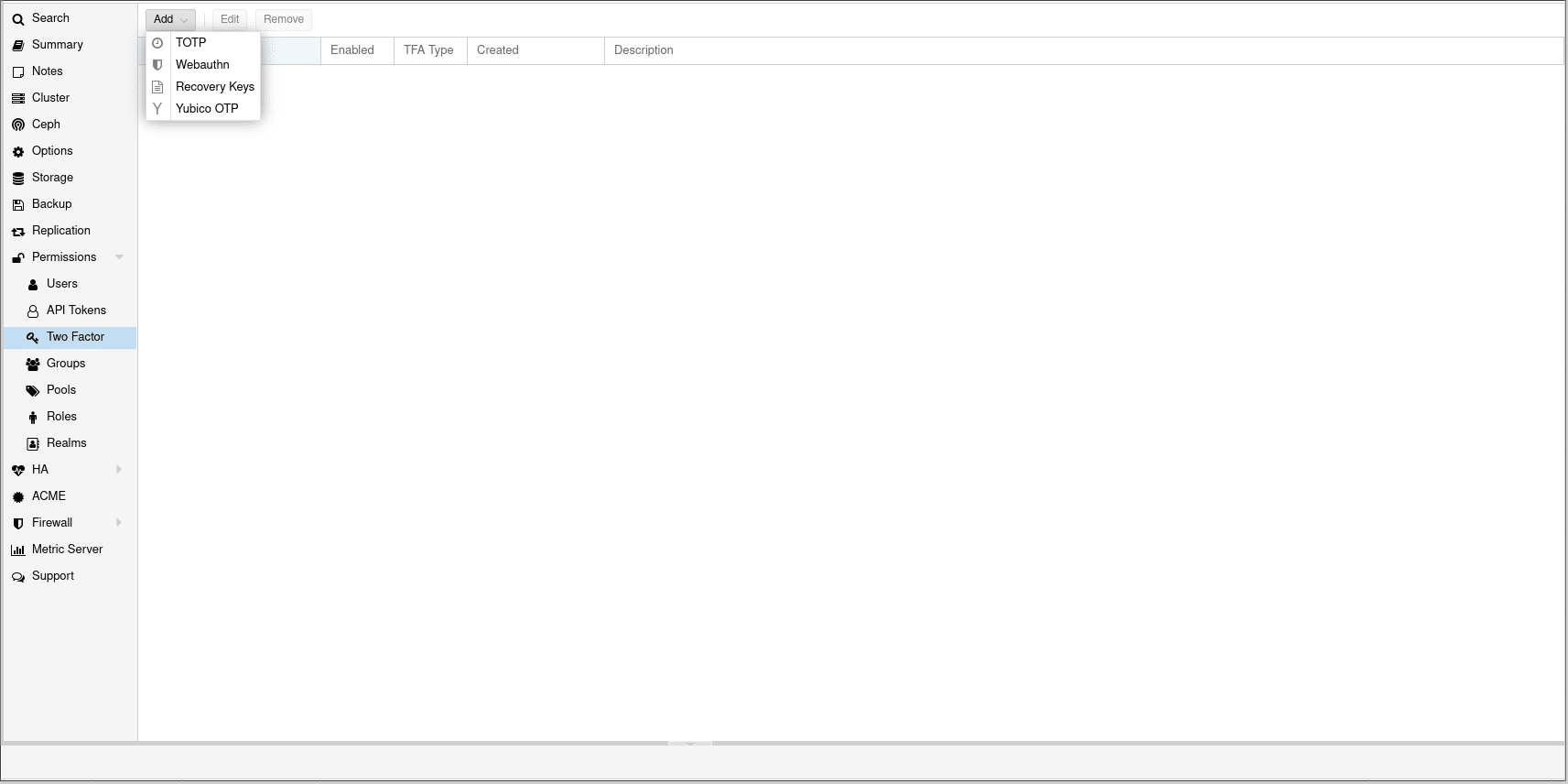
Combining this with creating users and groups, 2FA becomes a very powerful tool for creating secure and access-based permissions in your environment. This could even be taken further with Realms, allowing you to incorporate an LDAP or OpenID server, handing off authentication to Active Directory, OpenLDAP, or OpenID Connect, depending on your needs.
Proxmox VE 7.1 Security – 2FA Walk Through
To create a user that you can log in with there are two Realms to choose from:
- Using Proxmox VE authentication server
- Using Linux PAM standard authentication
Both have their own benefits and drawbacks. If you choose to use PAM, you must create a corresponding Linux user on the server. If you have an existing system in place, it works out well. If you choose to use the Proxmox VE authentication server, the user is shared across ALL servers in the Proxmox Datacenter and does NOT require a corresponding Linux user. Besides that, they are identical for our purposes.
For my use cases, the Proxmox VE authentication server works best, but you are free to choose whichever suits your needs. I will create a user named John Doe, with a password I can remember.
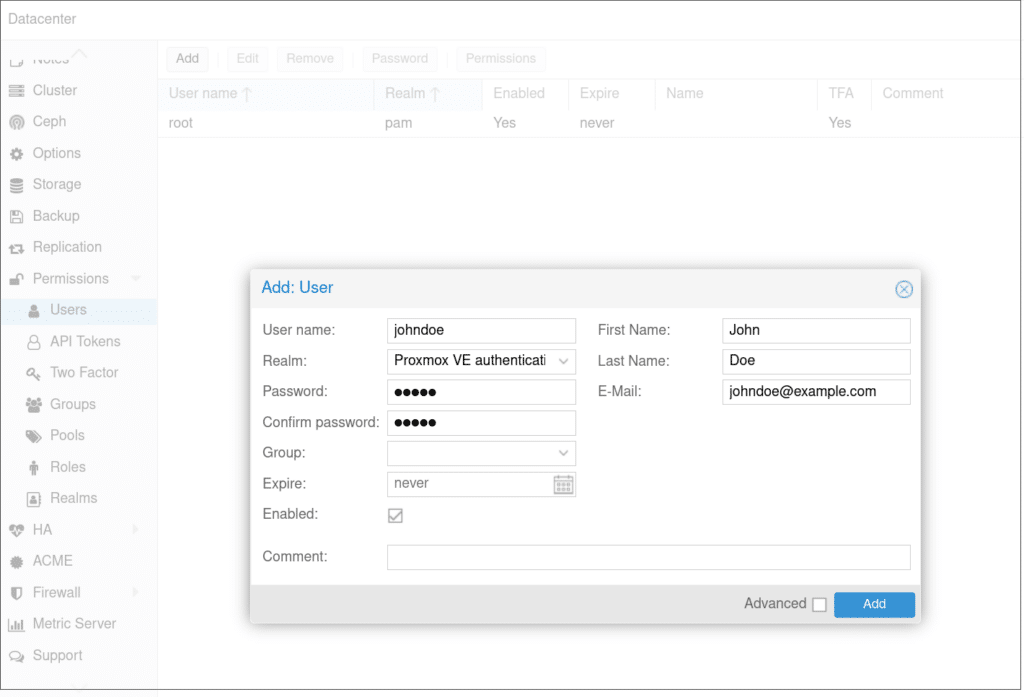
Next, I navigate to the 2FA page and I add TOTP authentication.
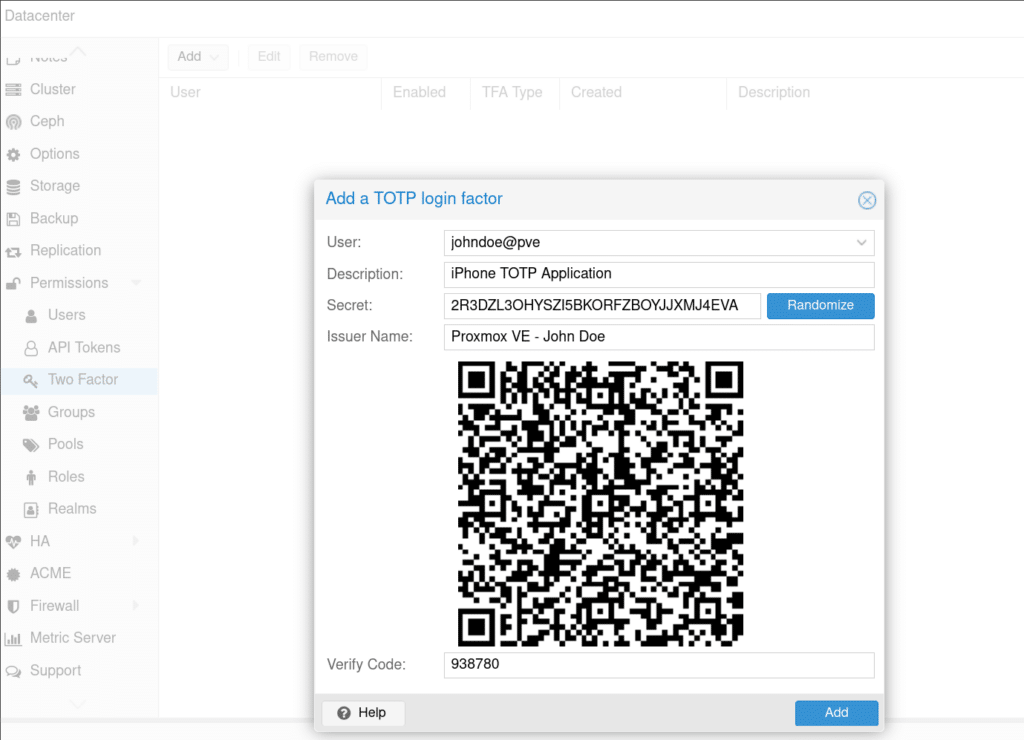
And finally, I can test that it works.
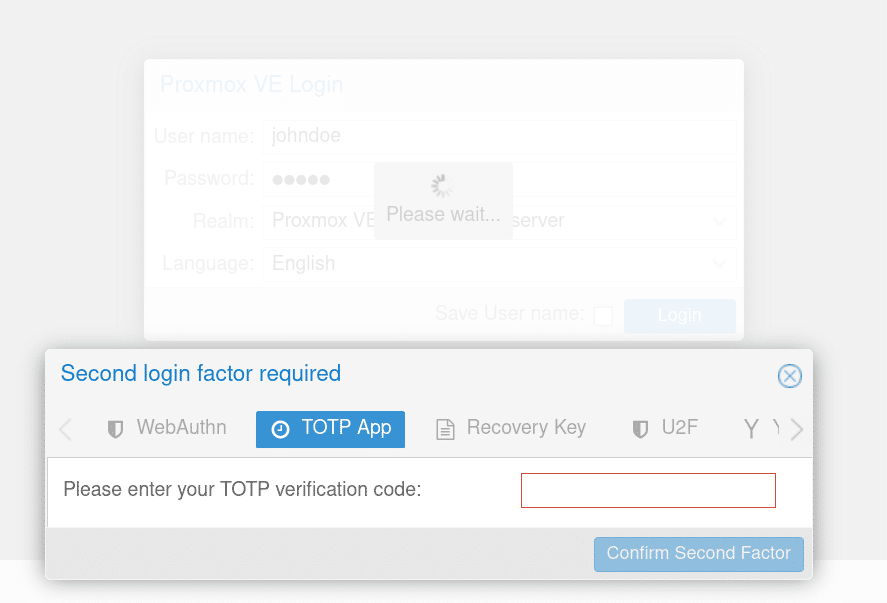
Conclusion
This update brought a lot of new features and improvements, but the Proxmox VE 7.1 security features are the most outstanding of them in my view. It is easy to see why Proxmox is used by industry professionals and homelabbers alike, as their team continues to produce quality work. Their additions of TPM, Secure Boot, and the 2FA improvements are no exception.




 Amazon
Amazon