QNAP has released a product security statement last week concerning the ransomware and brute-force attacks that have been targeting all networking devices. Those with a NAS accessible to the Internet without any protection are particularly at risk here. As such, QNAP urges that everyone using NAS solutions follow the security setting instructions in this article to make sure your end up with a Secure QNAP NAS.
It should be noted that the specific set of instructions from QNAP (covered below) better isolates your NAS from the internet, for better or worse. So, if you rely on it for apps and/or other stuff for remote access, doing this may disable those if to turn off all port forwarding access.
Secure QNAP NAS – Start with the Internet
First, verify whether or not your NAS is exposed to the Internet.
- Open Security Counselor on your QNAP device. This is accessed through QTS 5.0, QNAP’s web-based NAS operating system. In our StorageReview Lab, this app is not installed by default, so you might have downloaded it via the QTS App Center.
- If your NAS is exposed to the Internet and is at high risk, it will display the following message on the main dashboard: “The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP”
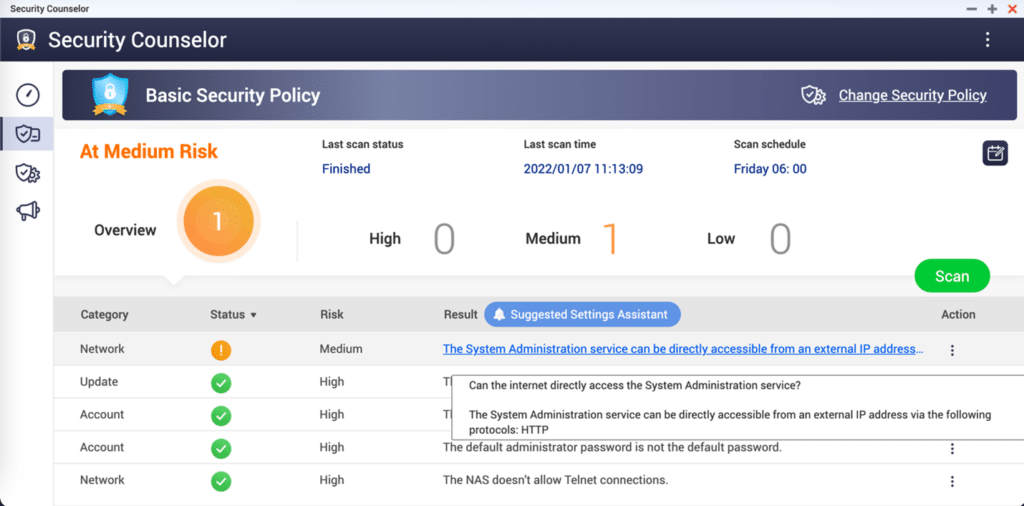
If this is the case, follow the instructions below:
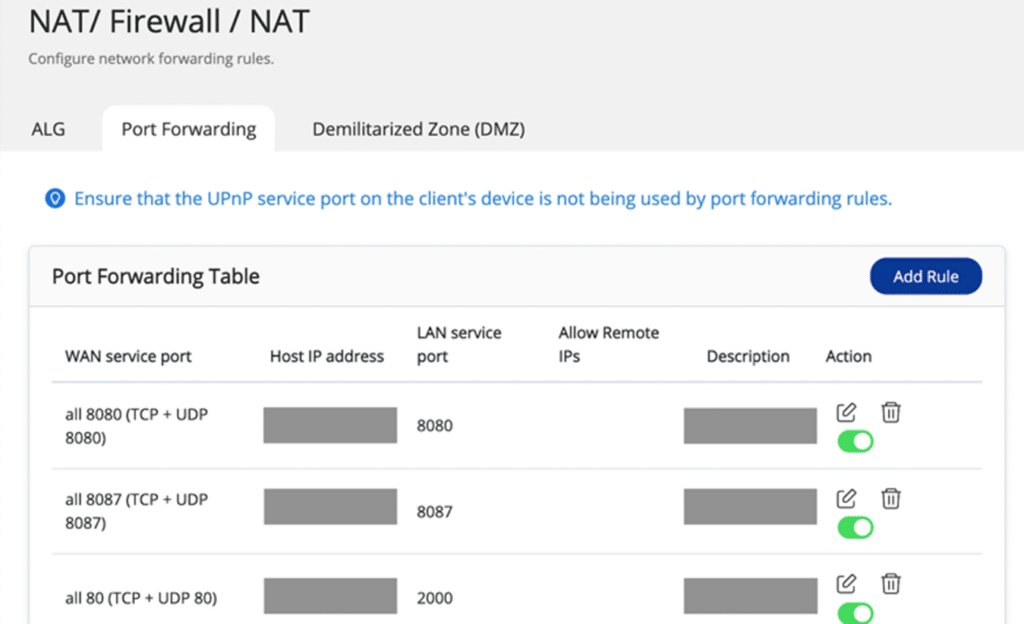
- Disable the port forwarding function of your router:
Navigate to the management section of your router’s web-based software to check the virtual server, NAT, or port forwarding settings. Once there, disable the port forwarding setting of the NAS management service port, which is port 8080 and 433 by default.QNAP has provided instructions on how to find out which ports on your router are exposed to the Internet.
- Disable the UPnP function on your QNAP NAS
Next, head back to QTS and launch myQNAPcloud via the main menu (under Systems). Click Auto Router Configuration and make sure that “Enable UPnP Port forwarding” is NOT selected. QNAP users can also access myQNAPcloud via the Internet.
As we indicated above, these steps to protect your device from QNAP may not be feasible for everyone, as it all depends on how you are using your NAS remotely. Taking some of these precautions might make your NAS a pointless device in certain use cases.
That said, there are some additional steps you can take to secure your platform from password-guessing attacks.
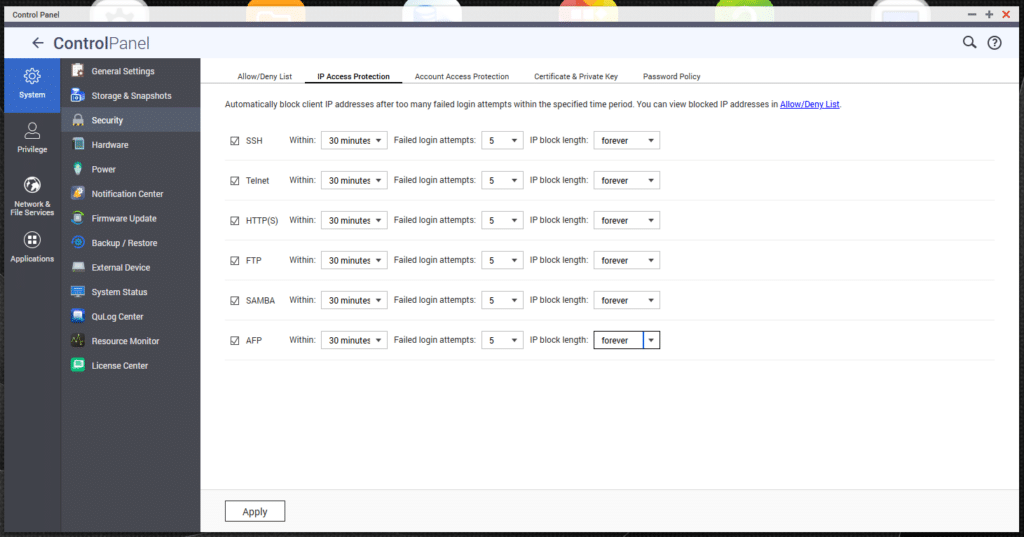
Navigate to Control Panel > System > Security section in QTS. Under the “IP Access Protection” tab, users should have all the options checked in see screenshot below. In addition, StorageReview recommends users have the following settings:
- “Within” figure to 30 minutes
- “Failed” attempts to 5
- IP block length to “forever”
Though network-connected devices are never 100% secure, these things will certainly go a long way in protecting your NAS from malware and other attacks.
You can also read our own article on how to Get a Secure NAS in 4 Easy Steps, which is a more detailed set of instructions on securing your home network.


 QNAP has provided instructions on how to find out
QNAP has provided instructions on how to find out 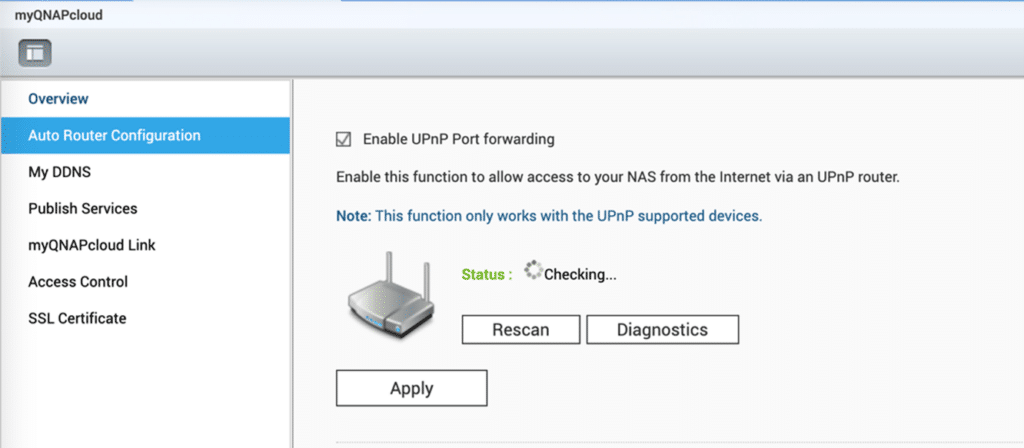


 Amazon
Amazon