Veeam Software has launched its new Veeam App for Microsoft Sentinel, which integrates seamlessly with the Veeam Data Platform. The Veeam App for Microsoft Sentinel enables organizations to detect, investigate, and respond to cyber threats and backup issues more easily, ensuring strong data protection and operational efficiency in Security Operations Centers (SOCs).
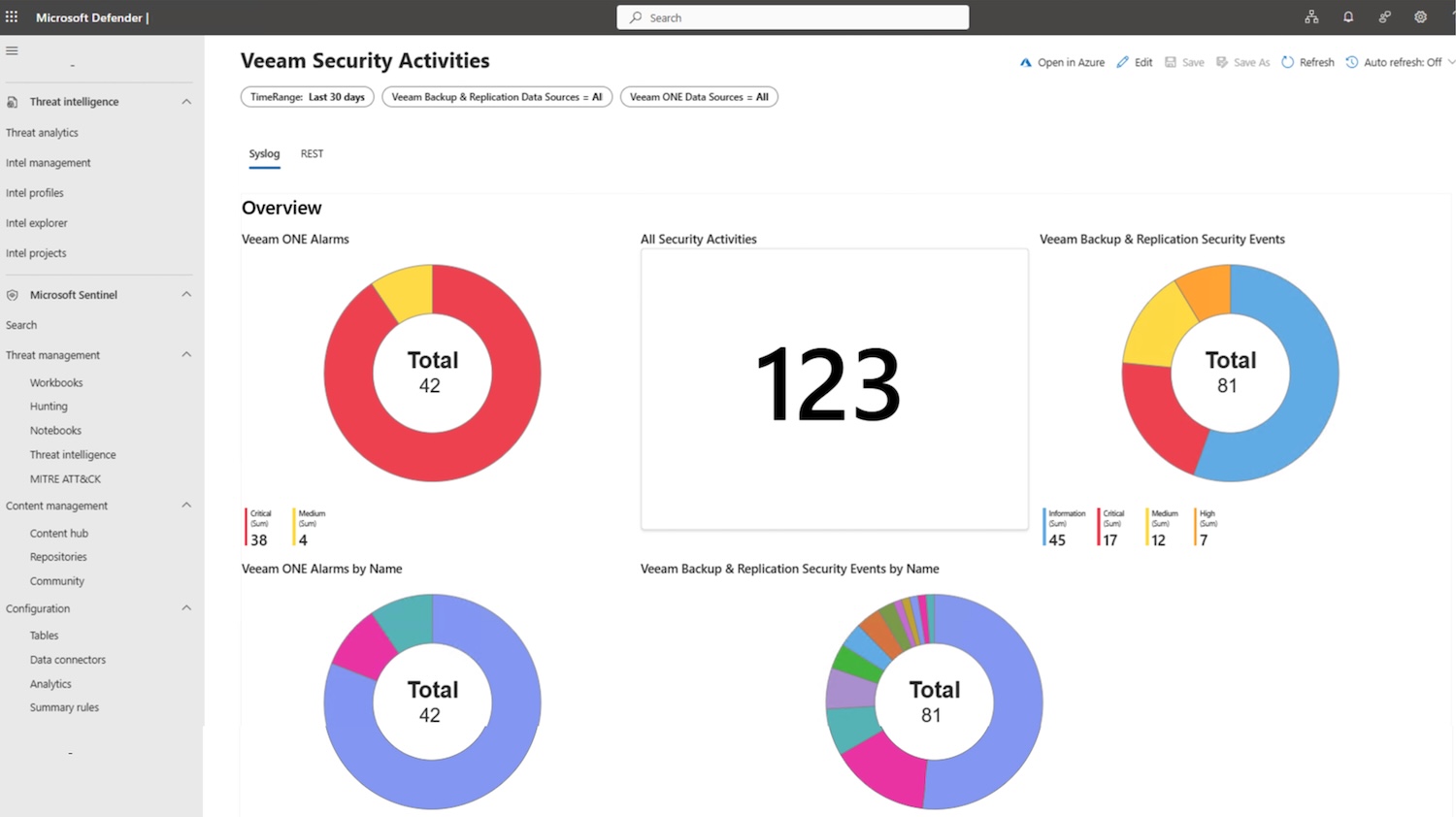
As cyberattacks increasingly target backup environments, many SOC teams lack significant visibility into their security systems. This puts organizations at risk for attacks on their last line of defense—their backups. The new Veeam App for Microsoft Sentinel helps address this issue by bringing backup intelligence directly into the SOC. This enables IT and security teams to collaborate in real-time, detect threats more quickly, and respond more effectively.
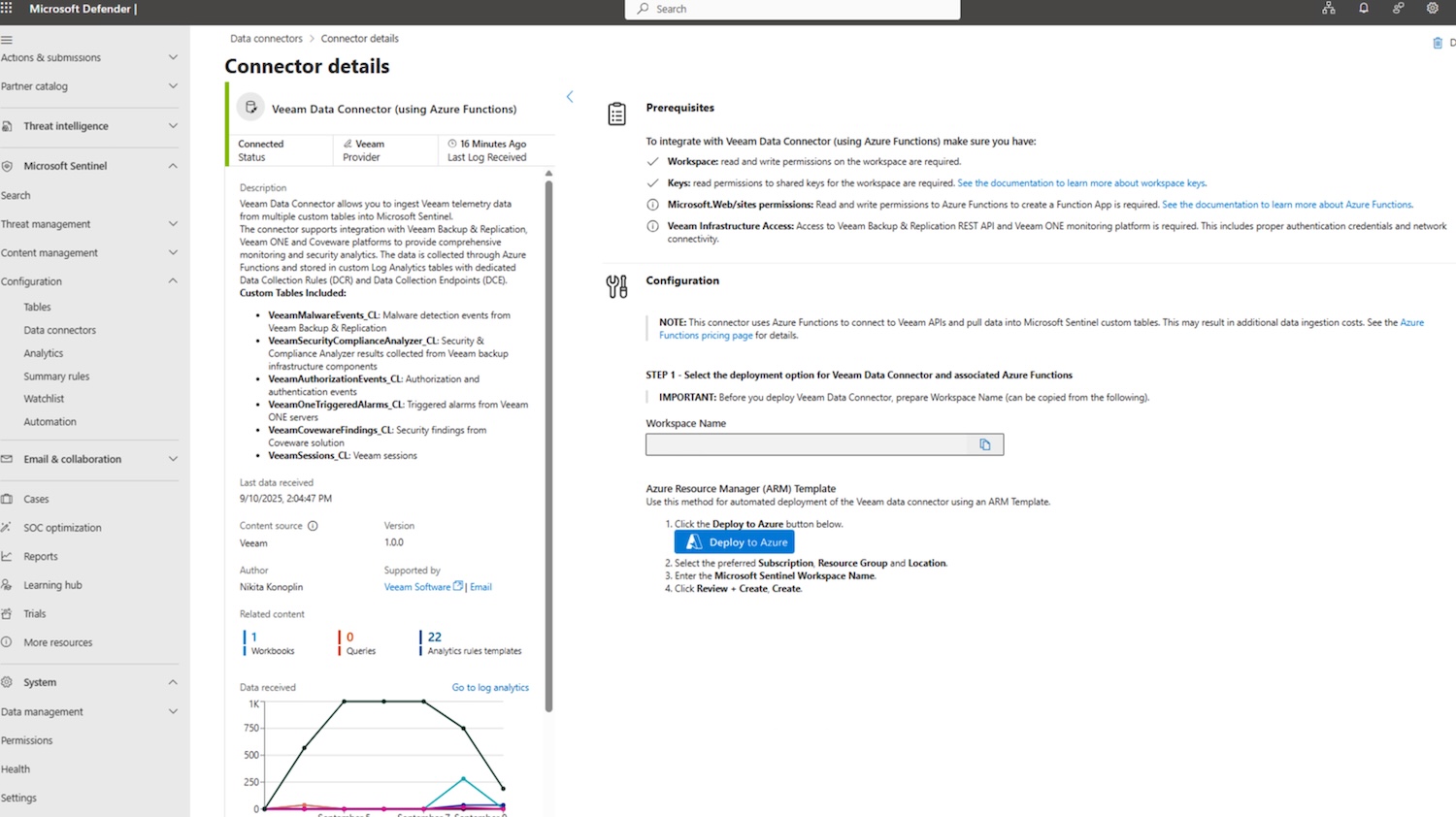
The new app provides a strong integration between Veeam Data Platform and Microsoft Sentinel, a cloud-based SIEM. It incorporates essential backup, threat, and ransomware information into security processes. Security teams can monitor and examine Veeam backup events, including tactics, techniques, and procedures (TTPs) identified by Veeam Recon Scanner, along with other key security signals. With two-way automation and flexible connections, teams can manage incidents, start restores, and automate recovery actions directly within Microsoft Sentinel.
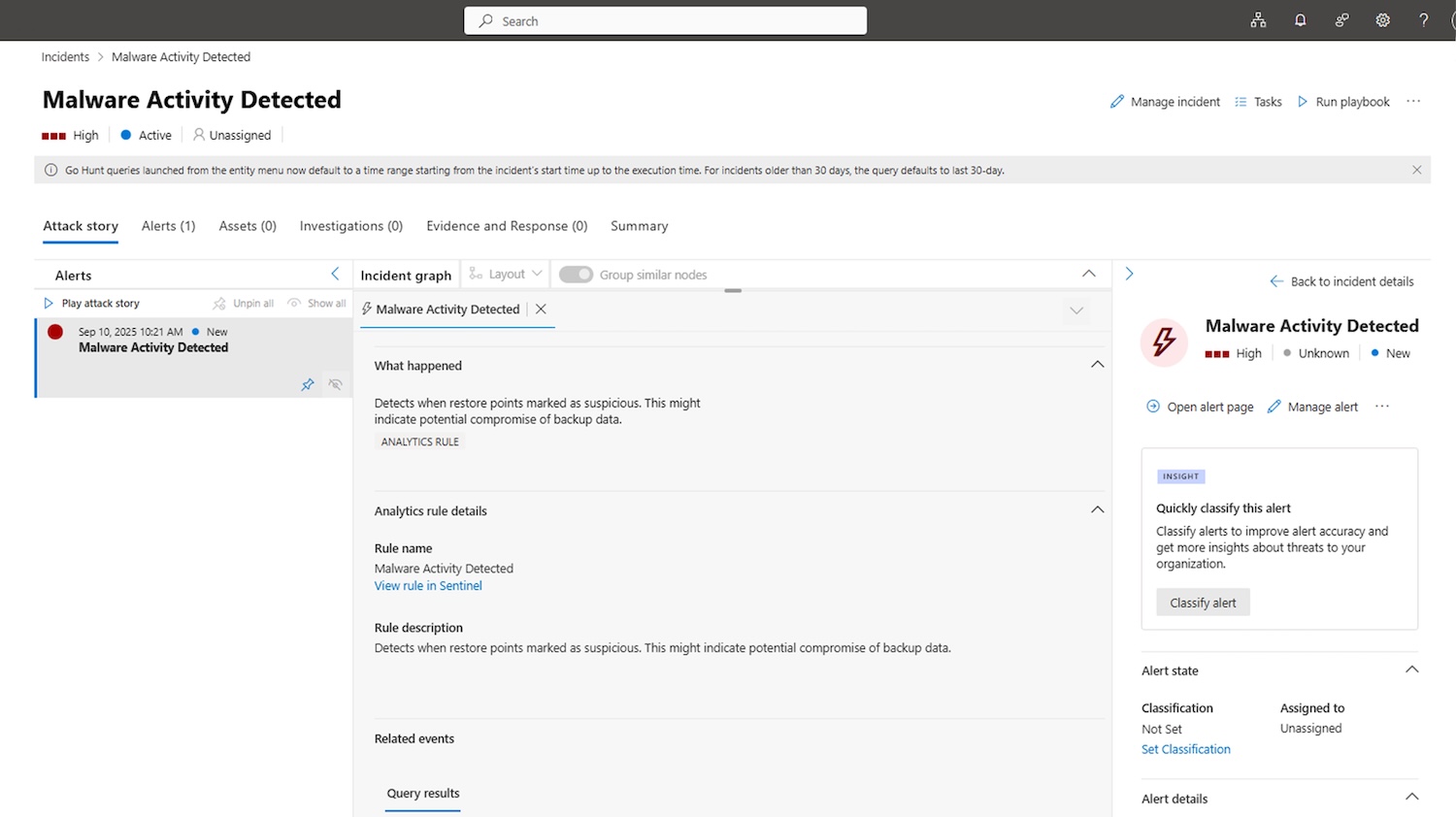
John Jester, Chief Revenue Officer of Veeam, stresses that data protection is essential in today’s cybersecurity landscape. He points out that their new app for Microsoft Sentinel improves security intelligence by quickly showing backup security events, suspicious activities, and ransomware threats. The solution supports SOC teams in making quick decisions to keep data safe and recoverable, even in the face of cyber threats.
Key features of the new Veeam App for Microsoft Sentinel include:
- Actionable Security Intelligence: This feature collects over 300 Veeam backup and security events, including job failures, suspicious activities, ransomware detections, and Recon Scanner findings. These events are mapped to MITRE ATT&CK for fast, proactive threat detection. This is Veeam’s first SIEM integration to highlight adversary TTPs and show early signs of compromise.
- Automated Response: Built-in playbooks and two-way API connections enable SOC teams to trigger restores, run malware scans, and initiate remediation workflows directly from Microsoft Sentinel. This speeds up responses and reduces manual work.
- Unified Visibility: Microsoft Sentinel-native dashboards display key backup and security information, including threat detections, restore activity, and job health, alongside existing SOC data. This centralized view enables faster investigations and improved compliance.
- Integrated IT and Security Collaboration: This feature removes barriers and streamlines incident response by combining IT and security workflows within the SOC. It encourages teamwork, accelerates investigations, and enhances ransomware defenses.
Veeam’s partnerships with top security operation tools enhance visibility into backup data, improve threat detection, and automate incident response. Veeam’s commitment to modern protection now smoothly extends into the Microsoft Sentinel ecosystem, helping organizations combat cyber threats and maintain data security in a complex digital world.
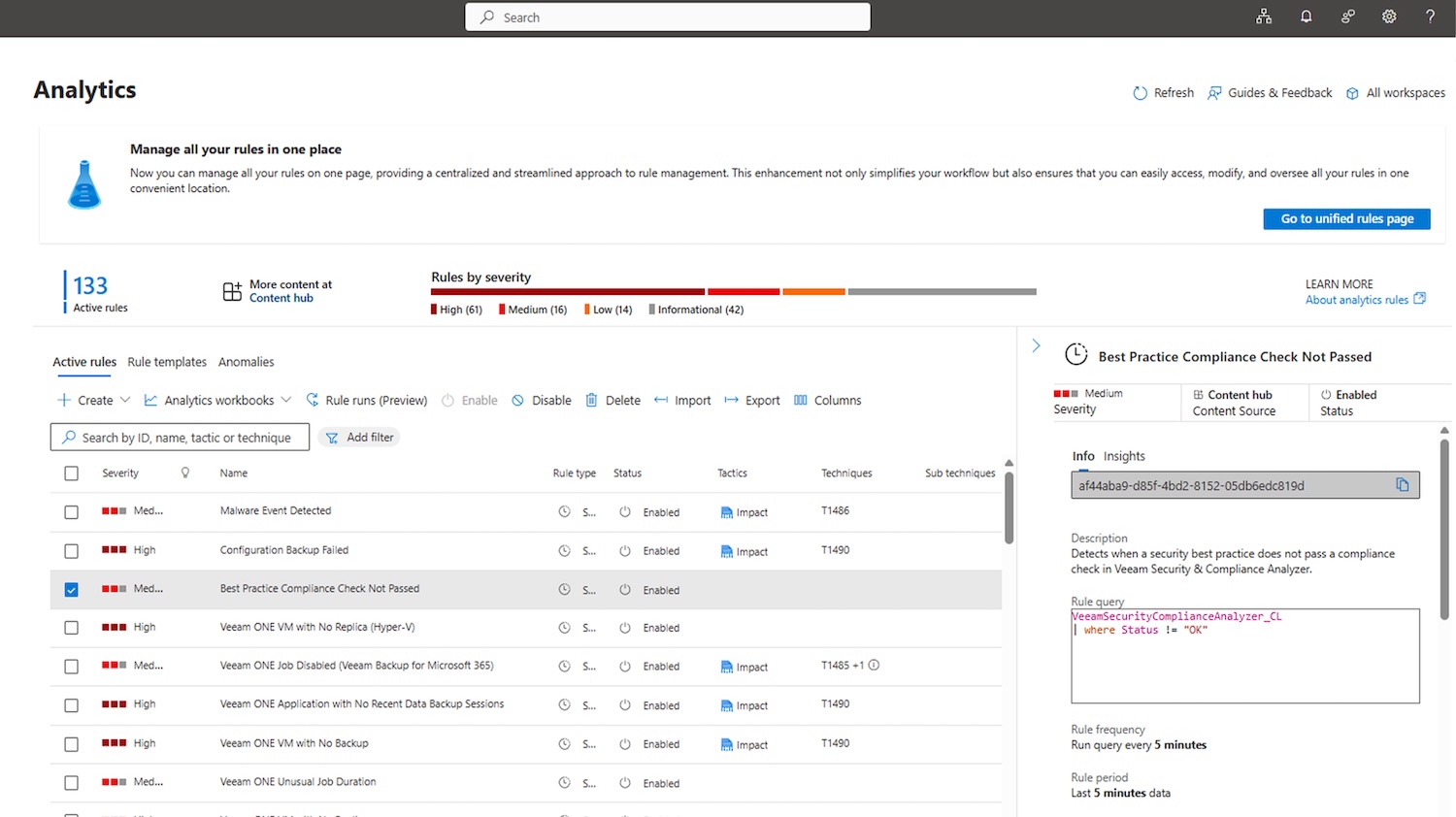
The Veeam App for Microsoft Sentinel is now available at no extra cost to Veeam Data Platform Advanced and Premium customers through Microsoft Marketplace and the Microsoft Sentinel Content Hub.




 Amazon
Amazon