According to a Veeam 2022 Ransomware Trends Report, cybercriminals are successfully encrypting an average of 47 percent of production data, with victims only able to recover 69 percent of the impacted data. The Ransomware report was unveiled today at VeeamON 2022, and Veeam has made it available for download.
According to the report, businesses are losing the battle when it comes to defending against ransomware attacks which found that 72 percent of organizations had partial or complete attacks on their backup repositories, dramatically impacting the ability to recover data without paying the ransom. The report also found that 80 percent of successful attacks targeted known vulnerabilities — reinforcing the importance of patching and upgrading software. Almost all attackers attempted to destroy backup repositories to disable the victim’s ability to recover without paying the ransom.
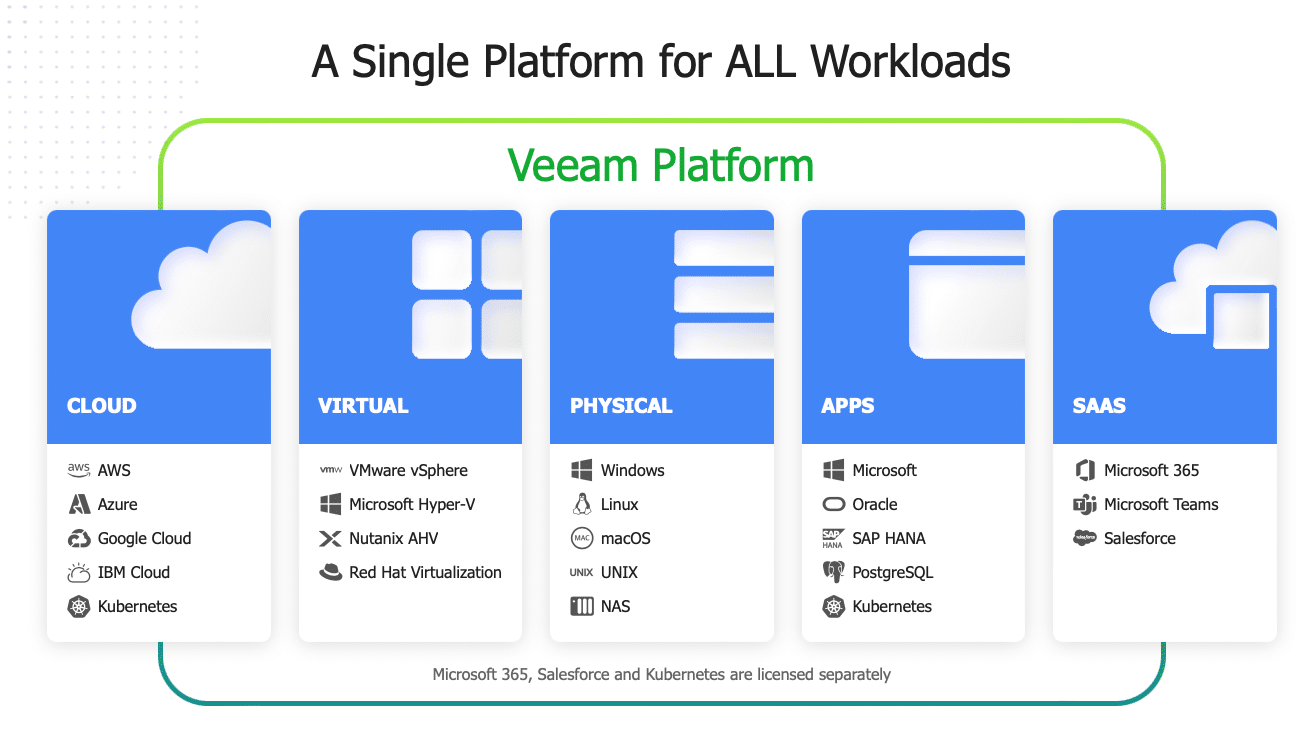
The Veeam 2022 Ransomware Trends Report reveals the results of an independent research firm that surveyed 1,000 IT leaders whose organizations had been successfully attacked by ransomware at least once during the past 12 months, making it one of the most extensive reports of its kind. This study is the first of its kind. It examines the key learnings from these incidents, their impact on IT environments, and the steps taken to implement Modern Data Protection strategies to ensure business continuity. The research project specifically surveyed four IT personas (CISOs, Security Professionals, Backup Administrators, and IT Operations) to understand cyber-preparedness alignment across organizations.
“Ransomware has democratized data theft and requires a collaborative doubling down from organizations across every industry to maximize their ability to remediate and recover without paying the ransom,” said Danny Allan, CTO at Veeam. “Paying cybercriminals to restore data is not a data protection strategy. There is no guarantee of recovering data, the risks of reputational damage and loss of customer confidence are high, and most importantly, this feeds a self-fulfilling prophecy that rewards criminal activity.”
Paying The Ransom Is Not A Recovery Strategy
Of the organizations surveyed, 76 percent of cyber-victims paid the ransom to end an attack and recover data. Unfortunately, while 52 percent paid the ransom and were able to recover data, 24 percent paid the ransom but were still not able to recover data — resulting in a one out of three chance that paying the ransom still leads to no data. Notably, 19 percent of organizations did not pay the ransom because they could recover their data. This is what the remaining 81percent of cyber-victims must aspire to — recovering data without paying the ransom.
“One of the hallmarks of a strong Modern Data Protection strategy is a commitment to a clear policy that the organization will never pay the ransom, but do everything in its power to prevent, remediate and recover from attacks,” added Allan. “Despite the pervasive and inevitable threat of ransomware, the narrative that businesses are helpless in the face of it is not an accurate one. Educate employees and ensure they practice impeccable digital hygiene; regularly conduct rigorous tests of your data protection solutions and protocols, and create detailed business continuity plans that prepare key stakeholders for worst-case scenarios.”
Prevention Requires Diligence From Both IT And Users
The “attack surface” for criminals is diverse. Cyber-villains most often first gain access to production environments through errant users clicking malicious links, visiting insecure websites, or engaging with phishing emails, exposing the avoidable nature of many incidents. After successfully gaining access to the environment, there was very little difference in the infection rates between data center servers, remote office platforms, and cloud-hosted servers.
In most cases, intruders took advantage of known vulnerabilities, including common operating systems and hypervisors, NAS platforms, and database servers, leaving no stone unturned and exploiting any unpatched or outdated software. Notably, significantly higher infection rates were reported by Security Professionals and Backup Administrators compared with IT Operations or CISOs, implying that “those closer to the problem see even more of the issues.”
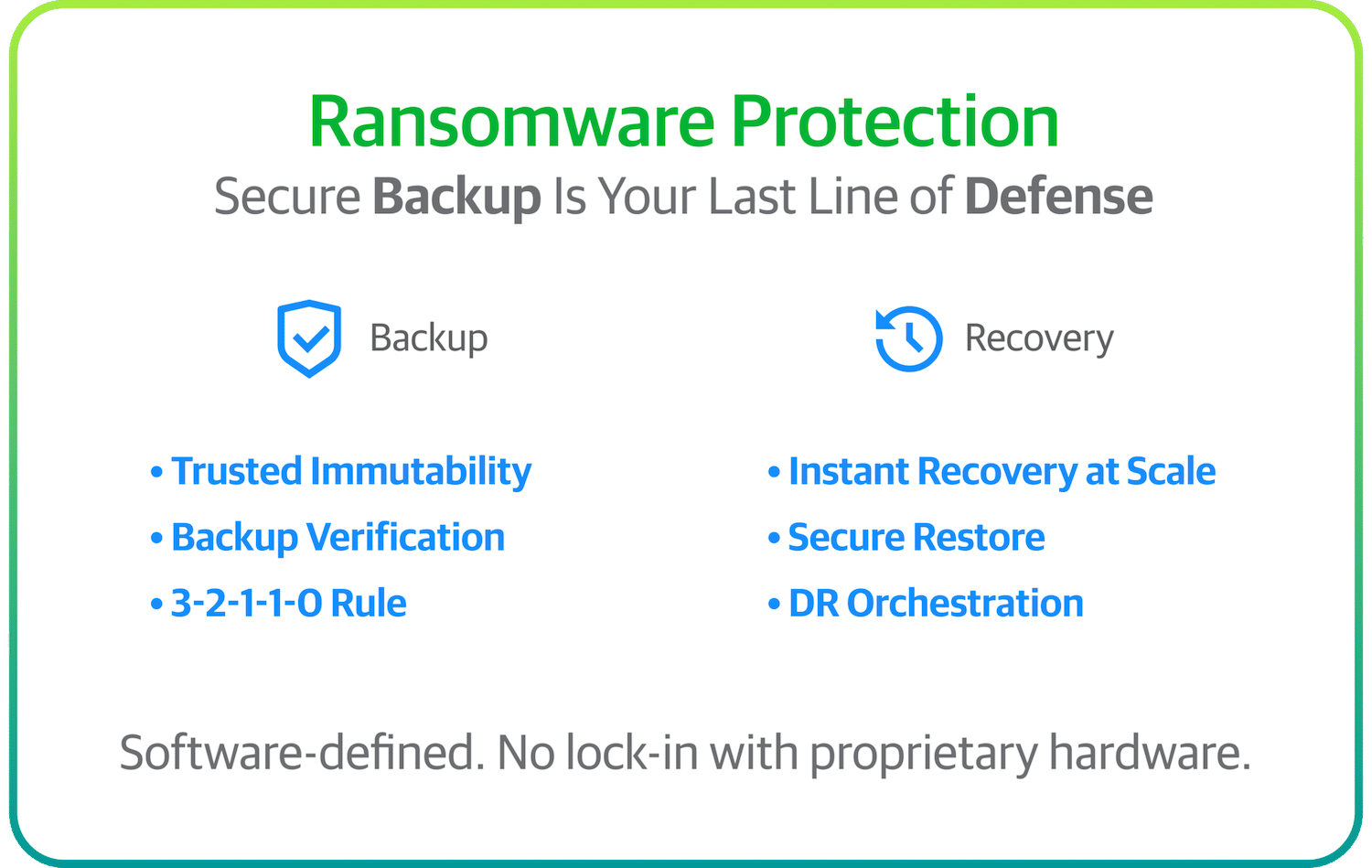
Remediation Starts With Immutability
Respondents to the survey confirmed that 94 percent of attackers attempted to destroy backup repositories, and in 72 percent of cases, this strategy was at least partially successful. This removal of an organization’s recovery lifeline is a popular attack strategy as it increases the likelihood that victims would have no other choice than to pay the ransom. The only way to protect against this scenario is to have at least one immutable or air-gapped tier within the data protection framework — which 95 percent of those we surveyed stated they now have. Many organizations reported having some level of immutability or air-gap media in more than one tier of their disk, cloud, and tape strategy.
Other key findings from the Veeam 2022 Ransomware Trends Report include:
- Orchestration matters: To proactively ensure the recoverability of their systems, one in six (16 percent) IT teams automate the validation and recoverability of their backups to ensure their servers are restorable. Then, during remediation of a ransomware attack, 46 percent of respondents use an isolated “sandbox” or staging/test area to ensure their restored data is clean before reintroducing the systems into production.
- Organization alignment must unify: 81 percent believe their organizations’ cyber and business continuity/disaster recovery strategies are aligned. However, 52 percent of respondents believe the interactions between these teams require improvement.
- Diversifying the repositories holds the key: Nearly all (95 percent) organizations have at least one immutable or air-gapped data protection tier. Seventy-four percent use cloud repositories that offer immutability, 67 percent use on-premises disk repositories with immutability or locking, and 22 percent use air-gapped tape. Immutable or not, organizations noted that in addition to disk repositories, 45 percent of production data is still stored on tape, and 62 percent goes into a cloud at some point in their data lifecycle.
About the Report
Veeam commissioned an independent market research company, Vanson Bourne, to conduct a survey of 1,000 unbiased IT leaders regarding the impact of ransomware within their environments and their IT strategies and data protection initiatives moving forward. Respondents represented organizations of all sizes from 16 countries in APJ, EMEA, and the Americas.
For more information, visit https://www.veeam.com.
Supporting Resources:




 Amazon
Amazon