Welcome to my penetration testing/software development/media editing/jack-of-all-trades lab! What started out two years ago is a crummy old Cisco switch and router, with a cheap r610, and no gigabit networking in sight (shudder), has grown to quite a decent little lab.

I’ll start with my big boy in the corner, my Threadripper workstation. With the Threadripper 3960x, 128GB of RAM, an AMD 5700xt, a Quadro RTX 4000, and a combined storage size of 8TB. She’s my main workhorse for anything that requires serious power thrown at it. For temporary CPU driven applications, I will spin up a virtual machine in VMware Workstation 20H2, and let my cycles chew away at any work that needs to be done.
Recently this has been compiling binaries for a security appliance I’ve been working on. GPU driven applications (let’s be real and call them CUDA driven applications) all get tossed at my RTX 4000.
This has included some machine learning applications, blender renders, and a perpetually running NVIDIA RTX Voice (it’s been a godsend, as my server room is my office). Oh yeah, and the poor little 5700XT is for gaming. When I get around to it.
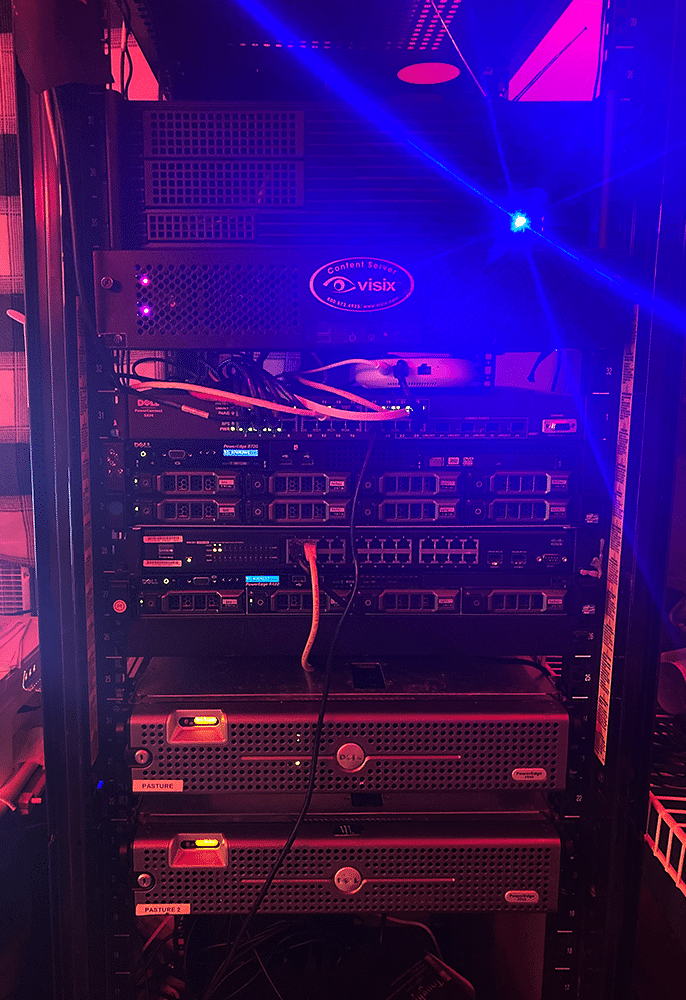
Now to the rack stack! Let me be the first to welcome you to the Habitual Lab! Let’s work our way from the bottom up! At the bottom we have Ye Olde Workhorses, (2) Poweredge 2950’s, running ESXi 6.5, with a combined 64GB of RAM between the two of them, their E5410 CPU’s are usually chugging away at any container applications I’m testing out. I’m not the hugest fan of containerizing everything, but with the way the industry is going, it’s necessary to know what’s up with them. Currently, it’s using VMware’s VIC, but I’ll play around with k8s, and docker swarms when I feel like it.
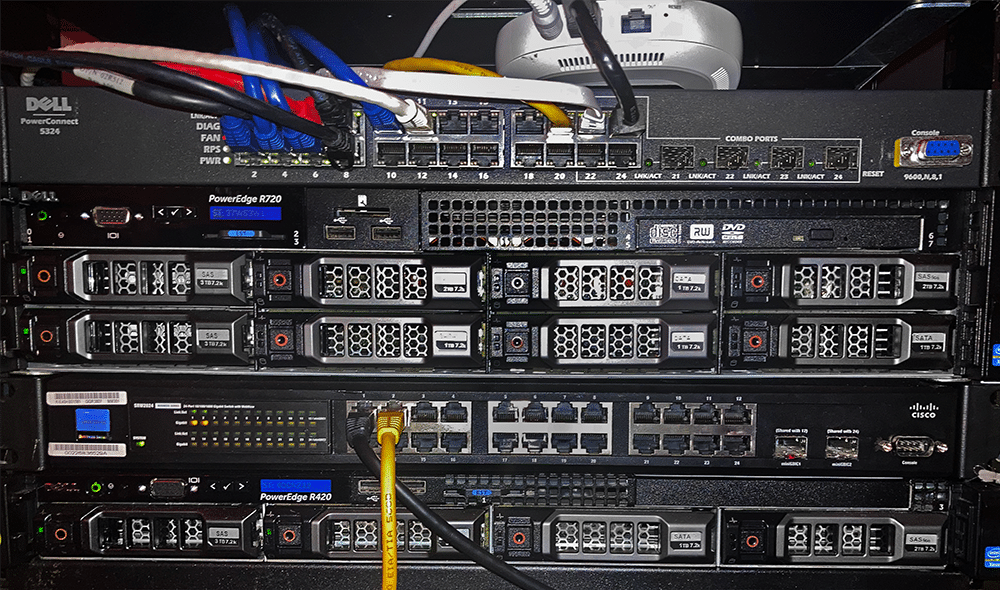
Moving up we have the core of my lab. Again, working bottom-up, we have my r420, installed with ESXi 6.7. With 64GB of RAM, and sporting paired E5-2407, and total storage of 6TB. It supports a sizeable portion of some of my lighter weight Linux VM’s and half of my Windows Domain. It also supports my edge router, a trusty PFsense VM.
Above that is my WAN switch. It’s just there to support a Security Onion sensor that I’m in the middle of building, so I get better coverage of all of my out-going traffic via SPAN ports. At least until I finally get around to buying a tap.
And then we come to Ol’ Faithful, my r720. Sporting a pair of trusty E5-2640’s, 192GB of RAM, and another 6TB of storage, and running ESXi 6.7, it’s my main lab workhorse. It runs a fully segregated penetration network, my development network, my core network, and the remaining portions of my Windows Domain, it’s a busy machine.
Where would a network be without some network storage? Next up we have my whitebox (aka slapped together from spare parts) NAS. Sporting a total of 5TB of storage, it might not be as big as the storage of some of my ESXi hosts, but it makes up for it by having a 4 NIC aggregated link, easily supporting traffic from all over my lab.
Combined with a RAID 5 array, that means anything being served from my NAS (usually) will never dip below 90-100 MBps, no matter how many things are being dragged. It runs a bare metal install of Server 2016, mainly because the easy integration with my domain makes an easy SSO solution for any over the network access.
Now, due to some oddness with putting an enterprise h610 raid controller with a consumer motherboard that doesn’t know what to do with PCIe devices that have independent ROM’s, the boot process is…. Interesting. Long story short, NAS is turned on, and halfway through POST, I plug the raid controller in. Let’s not talk about it anymore.
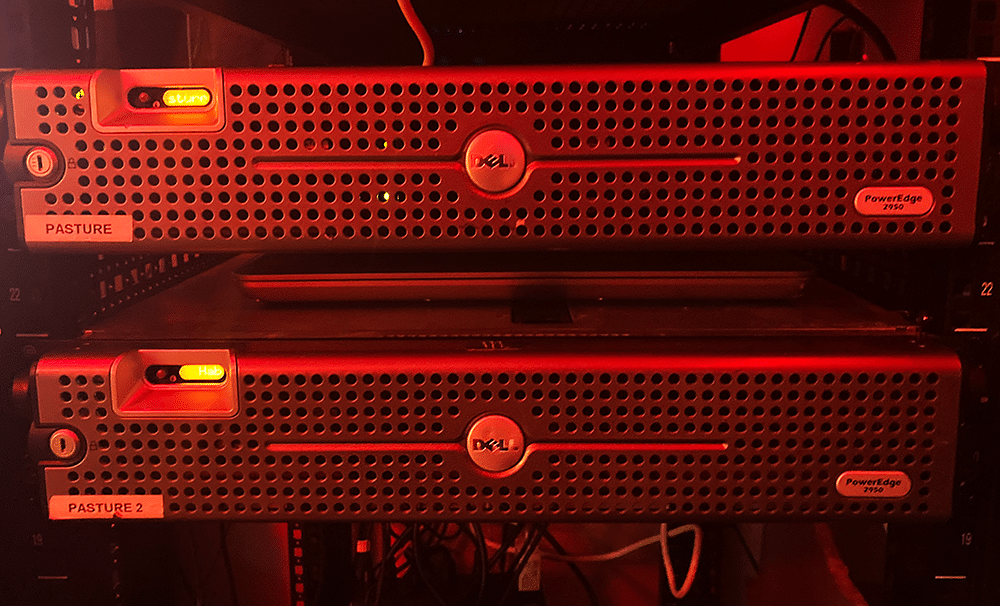
Finally on top is the gaming machine that has been put out to pasture. With an i7-4770k, 24GB of RAM, and an R9 390, it was quite the gaming rig back in the day. But it’s time of running AAA titles is over, and after being supplied with a 500 GB hard drive, it serves as a backup desktop, as well as running some of the monitors in my lab. It also has an ESXi host running on VMware Workstation, so I can migrate my critical services to it in case I need to do maintenance on my “real” servers.
By necessity, my environment is an extremely mixed one, about 35% Windows hosts in production, and the rest Linux hosts of some flavor. In the past, I defaulted to using Redhat 8 for my Linux hosts, but recently I’ve begun using Ubuntu 18.04 and 20.04. The transition hasn’t been for any specific reason, but it has been more convenient whenever I spin up a new host to not need to attach a subscription. For the Windows side of the house, I am fortunate enough to have a KMS key that is good for Server 2016 and below. While this means I can have essentially as many Windows boxes as I would like, it prevents me from adding a Server 2019 to my production network.
What do I do with this lab? Everything. By employment, I work as a Cybersecurity analyst/Security Engineer. But my job usually ends up with me touching every facet of the cyber world, from networking to infrastructure, to applications, to host/malware analysis. Having a capable lab has allowed me to remain flexible, and able to test and try every scenario I can think of, and then test out what I actually find on a customer’s network, without having to worry about breaking their stuff.
There’s also a “dirty net” isolated within. What’s here, you ask? Malware, viruses, and a lot of very bad practices. Separate from everything, and never connected to the internet, this is where I do some simple malware analysis. By monitoring both the host and network when a particular piece of malware is run, it assists me in developing methodologies to find the “bad stuff” out in the wild. I won’t profess to be a malware expert, but even a simple dynamic analysis from running malware along with monitoring software often yields simple but effective ways to identify it.
I also have a whole network that acts as a penetration testing lab, and it’s not just for me! I regularly invite both peers and mentees to hop on it, where everyone takes turns blue teaming and red teaming, to round out each person’s knowledge. The network itself is modeled after a stripped-down corporate network, complete with its own Windows Active Directory forest and domains, Linux hosts serving content, deliberately vulnerable hosts, and plenty of inside jokes spread around. Each user has a Kali Linux jump box as an attacker and a Windows 10 Admin box as a defender. It’s been a great way to keep my skills sharp in a more organic environment than you might find in a lot of training/courses.
– Corbett F.




 Amazon
Amazon